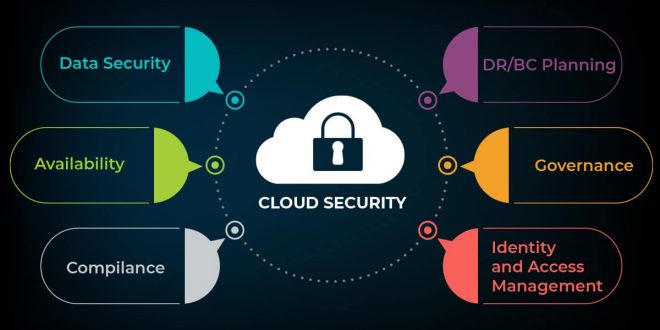
In the ever-evolving landscape of cloud computing, securing networks has become paramount. Cloud network security emerges as a critical aspect, safeguarding data, applications, and infrastructure in the virtual realm. This comprehensive guide delves into the fundamentals, best practices, and challenges associated with cloud network security, empowering you with the knowledge to protect your digital assets effectively.
Cloud network security encompasses a range of strategies and technologies designed to protect cloud-based networks from unauthorized access, data breaches, and other cyber threats. It involves implementing firewalls, intrusion detection systems, access control lists, and security monitoring tools to ensure the integrity and confidentiality of data.
Cloud Network Security Overview
Cloud network security is a critical aspect of cloud computing that involves protecting the network infrastructure, data, and applications deployed in the cloud. It ensures the confidentiality, integrity, and availability of cloud resources while maintaining compliance with regulatory and industry standards.
Implementing cloud network security brings numerous benefits, including enhanced protection against cyber threats, improved data privacy, reduced risk of data breaches, and simplified security management. However, it also presents challenges such as managing shared responsibility models, addressing multi-tenancy issues, and ensuring visibility and control across distributed cloud environments.
Examples of Cloud Network Security Solutions
- Firewalls:Virtual or physical devices that monitor and control incoming and outgoing network traffic based on predefined security rules.
- Intrusion Detection and Prevention Systems (IDS/IPS):Detect and prevent malicious activities on the network by analyzing traffic patterns and identifying suspicious behavior.
- Virtual Private Networks (VPNs):Secure tunnels that provide encrypted communication between remote users and the cloud environment.
- Web Application Firewalls (WAFs):Protect web applications from common attacks such as SQL injection, cross-site scripting, and denial-of-service attacks.
- Cloud Access Security Brokers (CASBs):Manage and enforce security policies for cloud applications and services, providing visibility and control across multiple cloud platforms.
Cloud Network Security Architecture
Cloud network security architecture is a framework that defines the security controls and mechanisms implemented within a cloud computing environment to protect the network and its resources from unauthorized access, threats, and vulnerabilities.
Components of Cloud Network Security Architecture
- Firewalls:Virtual or hardware-based devices that monitor and control network traffic based on predefined security rules. They block unauthorized access and prevent malicious traffic from entering or leaving the network.
- Intrusion Detection Systems (IDS):Network security devices that monitor network traffic for suspicious activities or patterns. They detect and alert administrators to potential security breaches or attacks.
- Access Control Lists (ACLs):Security mechanisms that define the permissions and access levels for users and devices within the network. They control who can access specific resources and services, preventing unauthorized access.
- Virtual Private Networks (VPNs):Encrypted tunnels that create secure connections between remote users or devices and the cloud network. They provide secure access to resources and protect data in transit.
- Network Segmentation:Dividing the network into smaller, isolated segments to limit the impact of security breaches. It prevents lateral movement of threats within the network.
- Cloud Security Posture Management (CSPM):Tools that monitor and assess the security posture of cloud environments. They identify misconfigurations, vulnerabilities, and compliance issues, enabling administrators to take proactive security measures.
Diagram of a Typical Cloud Network Security Architecture
[Insert a diagram of a typical cloud network security architecture here, including the components mentioned above and their interconnections.]Cloud Network Security Best Practices
Implementing effective cloud network security measures is crucial for protecting your organization’s data and infrastructure. Here are some best practices to consider:
Security Monitoring and Incident Response
Continuously monitoring your cloud network for suspicious activity and responding promptly to incidents is essential. Establish a comprehensive security monitoring plan that includes:
- Real-time threat detection and analysis
- Log analysis and correlation
- Incident response protocols and playbooks
- Regular security audits and vulnerability assessments
Cloud Network Security Best Practices Checklist
To ensure comprehensive cloud network security, follow these best practices:
- Implement a zero-trust approach to network access
- Segment your network into isolated subnets
- Use strong encryption for data in transit and at rest
- Enable multi-factor authentication for all user accounts
- Configure security groups and access control lists to restrict network access
- Implement intrusion detection and prevention systems (IDS/IPS)
- Monitor your network for suspicious activity and respond promptly to incidents
- Regularly update software and security patches
- Educate your users about cloud security best practices
- Conduct regular security audits and penetration testing
Cloud Network Security Challenges
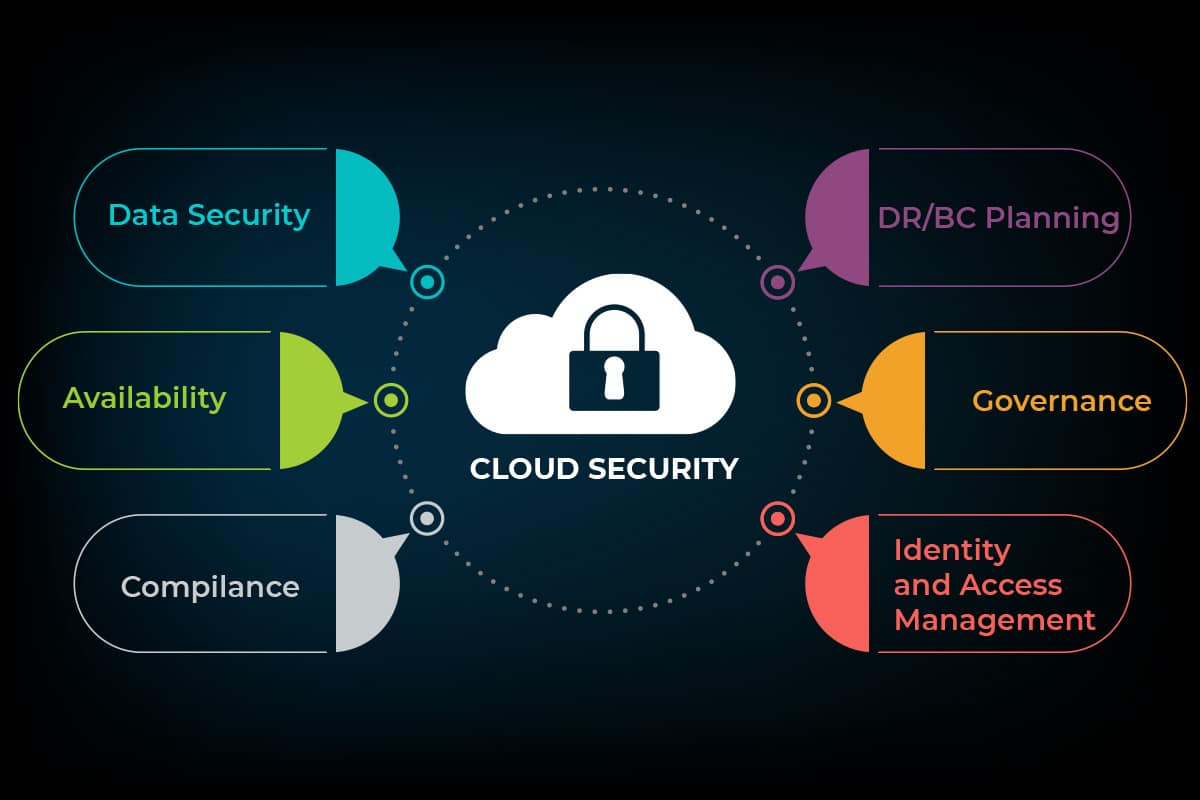
Implementing cloud network security poses unique challenges that organizations must address to ensure the confidentiality, integrity, and availability of their data and applications. These challenges stem from the inherent characteristics of cloud computing, such as shared infrastructure, dynamic resource allocation, and the potential for insider threats.
Unique Security Risks in Cloud Computing
*
-*Shared Infrastructure
Cloud environments often utilize shared infrastructure, which can increase the risk of data breaches and unauthorized access.
-
- -*Dynamic Resource AllocationCloud resources are allocated and released on demand, creating a dynamic environment that can be challenging to secure.
-*Insider Threats
Cloud environments can be accessed by multiple users, including administrators and end-users, increasing the potential for insider threats.
Recommendations for Overcoming Cloud Network Security Challenges
*
-*Implement Zero Trust
Establish a security model that assumes no implicit trust and requires verification of all users and devices.
-
- -*Use Micro-SegmentationDivide the network into smaller segments to limit the spread of threats and improve security.
-*Utilize Cloud-Native Security Tools
Leverage security tools specifically designed for cloud environments to enhance protection.
-*Monitor and Audit Regularly
Continuously monitor network activity and audit logs to detect and respond to potential threats.
-*Educate and Train Staff
Ensure that staff is aware of cloud security best practices and trained on appropriate security measures.
Cloud Network Security Tools
Cloud network security tools are essential for protecting cloud-based networks from a variety of threats. These tools can be used to monitor and control network traffic, detect and mitigate security breaches, and enforce security policies.
There are a variety of different cloud network security tools available, each with its own unique features and benefits. Some of the most popular cloud network security tools include:
Firewalls
Firewalls are one of the most basic and essential cloud network security tools. They act as a barrier between the cloud network and the outside world, and they can be used to control which traffic is allowed into and out of the network.
Firewalls can be configured to allow or deny traffic based on a variety of criteria, such as source IP address, destination IP address, port number, and protocol.
Intrusion Detection Systems (IDS)
IDSs are used to detect and monitor for suspicious activity on a cloud network. They can be used to identify a variety of different types of attacks, such as denial-of-service attacks, port scans, and malware infections.
IDSs can be configured to generate alerts when suspicious activity is detected. These alerts can be used to investigate the activity and take appropriate action.
Intrusion Prevention Systems (IPS)
IPSs are similar to IDSs, but they can also take action to prevent attacks from occurring. They can be used to block traffic that is identified as malicious or suspicious.
IPSs can be configured to block traffic based on a variety of criteria, such as source IP address, destination IP address, port number, and protocol.
Web Application Firewalls (WAFs)
WAFs are used to protect web applications from attacks. They can be used to block a variety of different types of attacks, such as SQL injection attacks, cross-site scripting attacks, and buffer overflow attacks.
WAFs can be configured to protect web applications from a variety of different types of attacks. They can be used to block traffic based on a variety of criteria, such as source IP address, destination IP address, port number, and protocol.
Security Information and Event Management (SIEM) Systems
SIEM systems are used to collect and analyze security data from a variety of sources. They can be used to identify trends and patterns in security data, and they can help to identify and mitigate security risks.
SIEM systems can be used to collect data from a variety of sources, such as firewalls, IDS/IPS, and WAFs.
Cloud Access Security Brokers (CASBs)
CASBs are used to control access to cloud resources. They can be used to enforce security policies, and they can help to prevent unauthorized access to cloud resources.
CASBs can be used to control access to cloud resources based on a variety of criteria, such as user identity, role, and location.
| Tool | Features | Benefits |
|---|---|---|
| Firewalls | Control traffic based on source/destination IP, port, protocol | Protect networks from unauthorized access |
| IDSs | Detect suspicious activity on networks | Identify potential attacks |
| IPSs | Detect and block malicious traffic | Prevent attacks from occurring |
| WAFs | Protect web applications from attacks | Block SQL injection, cross-site scripting, buffer overflow attacks |
| SIEM Systems | Collect and analyze security data | Identify trends, patterns, and security risks |
| CASBs | Control access to cloud resources | Enforce security policies, prevent unauthorized access |
Cloud Network Security Case Studies
Cloud network security case studies provide valuable insights into how organizations have successfully implemented cloud network security measures to protect their IT infrastructure and data. These case studies highlight the challenges faced by organizations, the solutions they implemented, and the benefits they achieved by enhancing their cloud network security posture.
Case Study: Company XYZ
Company XYZ, a leading e-commerce retailer, faced challenges in securing its rapidly growing cloud infrastructure. They implemented a comprehensive cloud network security solution that included:
- Implementing a cloud-based firewall to control network traffic and prevent unauthorized access.
- Deploying an intrusion detection system (IDS) to monitor network traffic for suspicious activities.
- Using a cloud access security broker (CASB) to manage access to cloud resources and enforce security policies.
As a result of these measures, Company XYZ significantly reduced the number of security incidents and improved the overall security of its cloud infrastructure. They also achieved cost savings by consolidating their security tools and reducing the need for manual security processes.
Cloud Network Security Trends
The cloud network security landscape is constantly evolving, with new threats and challenges emerging all the time. To stay ahead of the curve, it’s important to be aware of the latest trends in cloud network security and how they may impact your organization.
Impact of New Technologies on Cloud Network Security
The adoption of new technologies, such as artificial intelligence (AI), machine learning (ML), and the Internet of Things (IoT), is having a significant impact on cloud network security. These technologies can be used to improve the security of cloud networks, but they can also create new vulnerabilities that need to be addressed.
- AI and ML can be used to detect and respond to threats more quickly and effectively.
- IoT devices can be used to collect data that can be used to improve the security of cloud networks.
- However, new technologies can also create new vulnerabilities that need to be addressed.
Predictions for the Future of Cloud Network Security
The future of cloud network security is likely to be characterized by the following trends:
- Increased adoption of AI and ML for threat detection and response.
- Greater use of IoT devices to collect data for security purposes.
- Development of new security tools and technologies to address the challenges of cloud computing.
By staying ahead of these trends, organizations can improve the security of their cloud networks and protect their data from threats.
Final Conclusion
Embracing cloud network security is not merely an option but a necessity in today’s digital environment. By understanding the concepts, best practices, and challenges Artikeld in this guide, you can effectively secure your cloud networks, ensuring the protection of your sensitive data and the continuity of your business operations.
Originally posted 2024-05-17 17:35:42.
 Bussines News Daily
Bussines News Daily